Vulnerability Trends Summary
As part of our monthly vulnerability trends, this report shows the monthly top 10 trends on security vulnerabilities and how hackers, malware, and exploit kits are exploiting those vulnerabilities. To demonstrate, we assign vulnerability trends value as a percentage of how each vulnerability is significantly gaining the attention of cybersecurity communities, attackers, together with malware. In either case, companies can benefit from the report to have more cyber threat insights and relatively anticipate attacks wave that might target their public assets in the following months.
Subscribe to the monthly vulnerability digest report by clicking here.
The following chart shows the trends.
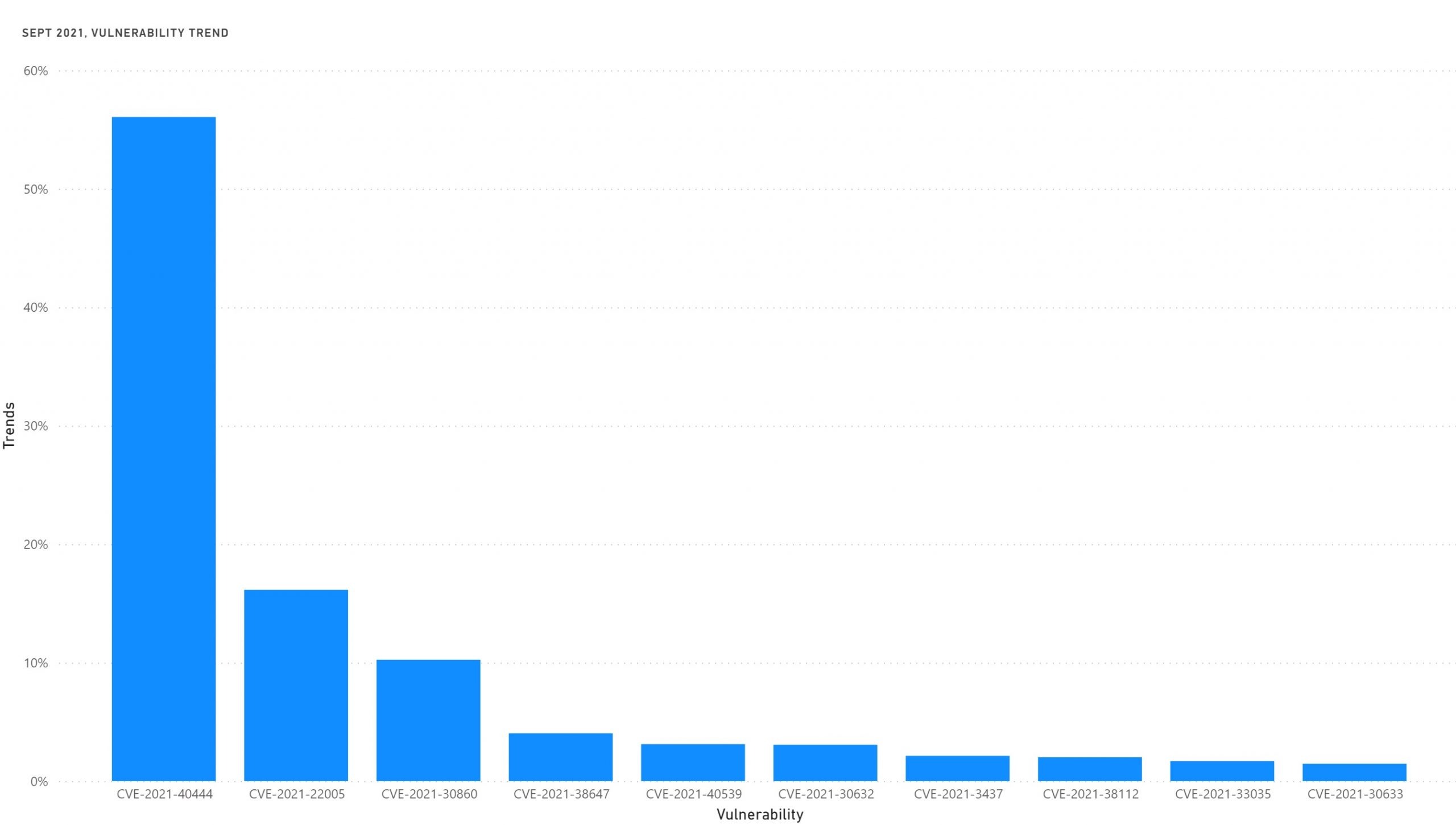

September 2021 has many discovered remote execution vulnerabilities. The most important one was MSHTML RCE in the Microsoft browser engine used in Office.
Other RCE vulnerabilities were in Chrome, vCenter, OpenOffice, and others.
The following table shows the details of the trends.
| CVE | Vulnerability | Publish Date | Exploited | Trends* |
| CVE-2021-40444 | Microsoft MSHTML RCE | 07/09/2021 | Yes | 56% |
| CVE-2021-22005 | Arbitrary file upload in vCenter | 21/09/2021 | Yes | 16% |
| CVE-2021-30860 | Remote Code Execution in iOS/iPadOS/macOS | 24/08/2021 | Yes | 10% |
| CVE-2021-38647 | Remote Code Execution in OMI | 14/09/2021 | Yes | 4% |
| CVE-2021-40539 | Authentication Bypass in ManageEngine ADSelfService Plus | 07/09/2021 | Yes | 3% |
| CVE-2021-30632 | Remote Code Execution in Chrome | 13/09/2021 | Yes | 3% |
| CVE-2021-3437 | Privilege Escalation in HP OMEN | 14/09/2021 | No | 2% |
| CVE-2021-38112 | Code Execution in AWS WorkSpaces Client | 21/09/2021 | Yes | 2% |
| CVE-2021-33035 | Code Execution in Apache OpenOffice | 18/09/2021 | Yes | 2% |
| CVE-2021-30633 | Remote Code Execution in Chrome | 13/09/2021 | No | 2% |
Subscribe to the monthly vulnerability digest report by clicking here.
1. CVE-2021-40444 Microsoft MSHTML RCE
A remote code execution vulnerability was detected in MSHTML browser rendering engine of Microsoft. An attacker could craft a malicious ActiveX control to be used by a Microsoft Office document to run malicious code in the user context.
2. CVE-2021-36958 Arbitrary File Upload in vCenter
The vCenter Server contains an arbitrary file upload vulnerability in the Analytics service. A malicious actor with network access to port 443 on vCenter Server may exploit this issue to execute code on vCenter Server by uploading a specially crafted file.
3. CVE-2021-30860 Remote Code Execution in iOS/iPadOS/macOS
An integer overflow vulnerability exists in CoreGraphics the common component in iOS/iPadOS/macOS which allows an attacker to exploit the target using a crafted PDF file.
4. CVE-2021-38647 Remote Code Execution in OMI
Remote code execution in Open Management Infrastructure (OMI) is used in Linux VMs of Azure and many images that utilize this version of Linux. This vulnerability is dubbed as OMIGOD.
5. CVE-2021-40539 Authentication Bypass in ManageEngine ADSelfService Plus
An authentication bypass vulnerability in ManageEngine ADSelfService Plus affecting the REST API URLs that could result in remote code execution.
6. CVE-2021-30632 Remote Code Execution in Chrome
A use-after-free bug exists in Chrome that results in remote code execution when a user visits a malicious website that exploits this vulnerability.
7. CVE-2021-3437 Privilege Escalation in HP OMEN
Security vulnerabilities have been identified in an OMEN Gaming Hub SDK package which may allow escalation of privilege and/or denial of service.
8. CVE-2021-30563 Code Execution in AWS WorkSpaces Client
In the Amazon AWS WorkSpaces client on Windows, argument injection in the workspaces:// URI handler can lead to remote code execution because of the Chromium Embedded Framework (CEF) –gpu-launcher argument.
9. CVE-2021-33035 Code Execution in Apache OpenOffice
A code execution vulnerability exists in Apache OpenOffice allows an attacker to exploit this vulnerability by a crafted dbf file.
10. CVE-2021-30633 Remote Code Execution in Chrome
A use-after-free bug exists in Chrome that results in remote code execution when a user visits a malicious website that exploits this vulnerability.
| CVSS Rate | 4.1 Medium |
| Exploited | No |
| Links | https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-30633 |
ScanTitan is the leading website security portal that offers website vulnerability scanning, website malware scanning, uptime monitoring, cyber brand monitoring, defacement monitoring, and continuous threat monitoring and alerting.
Now you can find the latest Scantitan promotions through our official coupon store.
Fuente obtenida de: https://scantitan.com/blog/monthly-vulnerability-digest/september-2021-vulnerability-trends/