Using the Silent Push App and API to Find Punycode Domains
Yesterday, a security engineer for the privacy-focused Brave web browser, tweeted about a domain impersonating Brave that was promoted through Google ads.
The domain was bravė[.]com.
Note the accent on the e, which distinguishes it from brave[.]com, the domain it was impersonating.
This is an example of an Internationalized Domain Name (IDN), a domain name that includes non-ASCII characters. Such domains have an ASCII representation that starts with xn-- and use punycode to convert from ASCII to unicode and vice versa. The ASCII representation of the impersonating domain is xn--brav-yva[.]com.
When IDNs are used to impersonate existing domains, one speaks of a homograph or homoglyph attack. Other than the use of accents on Latin characters, this also includes using similar-looking characters from non-Latin alphabets, such as using the Greek α instead of the Latin a. Though not incredibly common in practice, such attacks do exist and security researchers have warned about them for more than a decade.
The bravė[.]com or xn--brav-yva[.]com domain was registered through NameCheap in June and is hosted at 185.198.166.104, which belongs to ITLDC, a Bulgarian cloud provider with servers in a number of countries.
Using the Silent Push app, the user can see what else is hosted there:
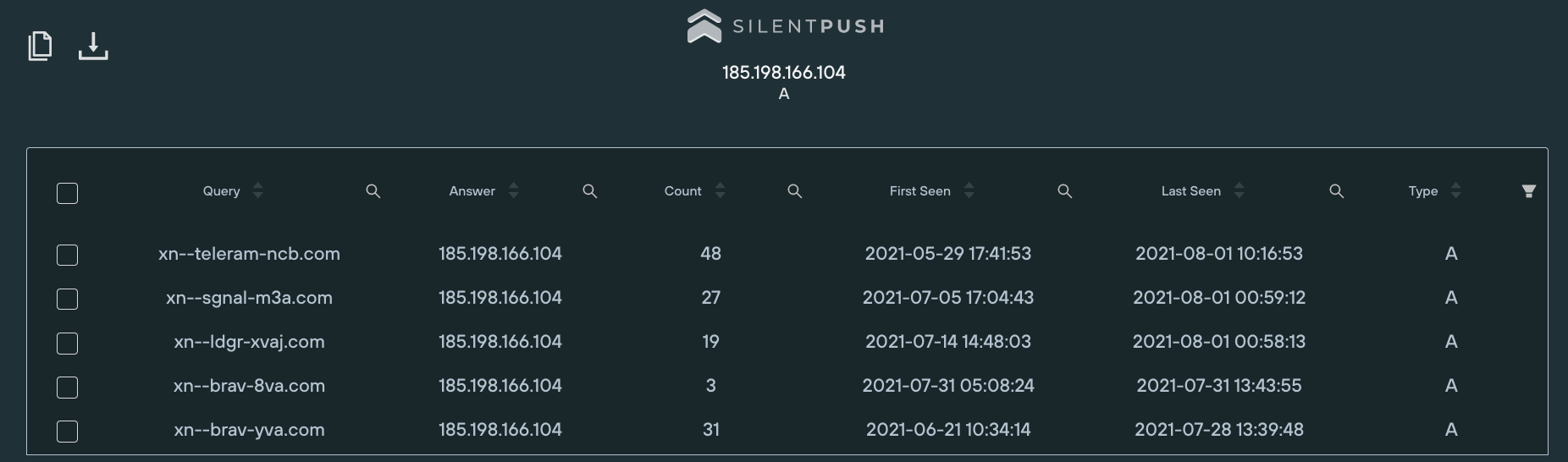
Three more domain names were found, all IDNs: xn--ldgr-xvaj[.]com, xn--sgnal-m3a[.]com and xn--teleram-ncb[.]com. The unicode representations of these domains are lędgėr[.]com, sīgnal[.]com and teleģram[.]com respectively, presumably impersonating cryptocurrency wallet maker Ledger and messaging apps Signal and Telegram. (I say ‘presumably’ because signal[.]com and telegram[.]com aren’t actually linked to the respective messaging apps.)
These other three domains were also registered at NameCheap. Using the Silent Push passive DNS, it was found that none of the domains had been seen at another IP address, so the user cannot pivot any further.
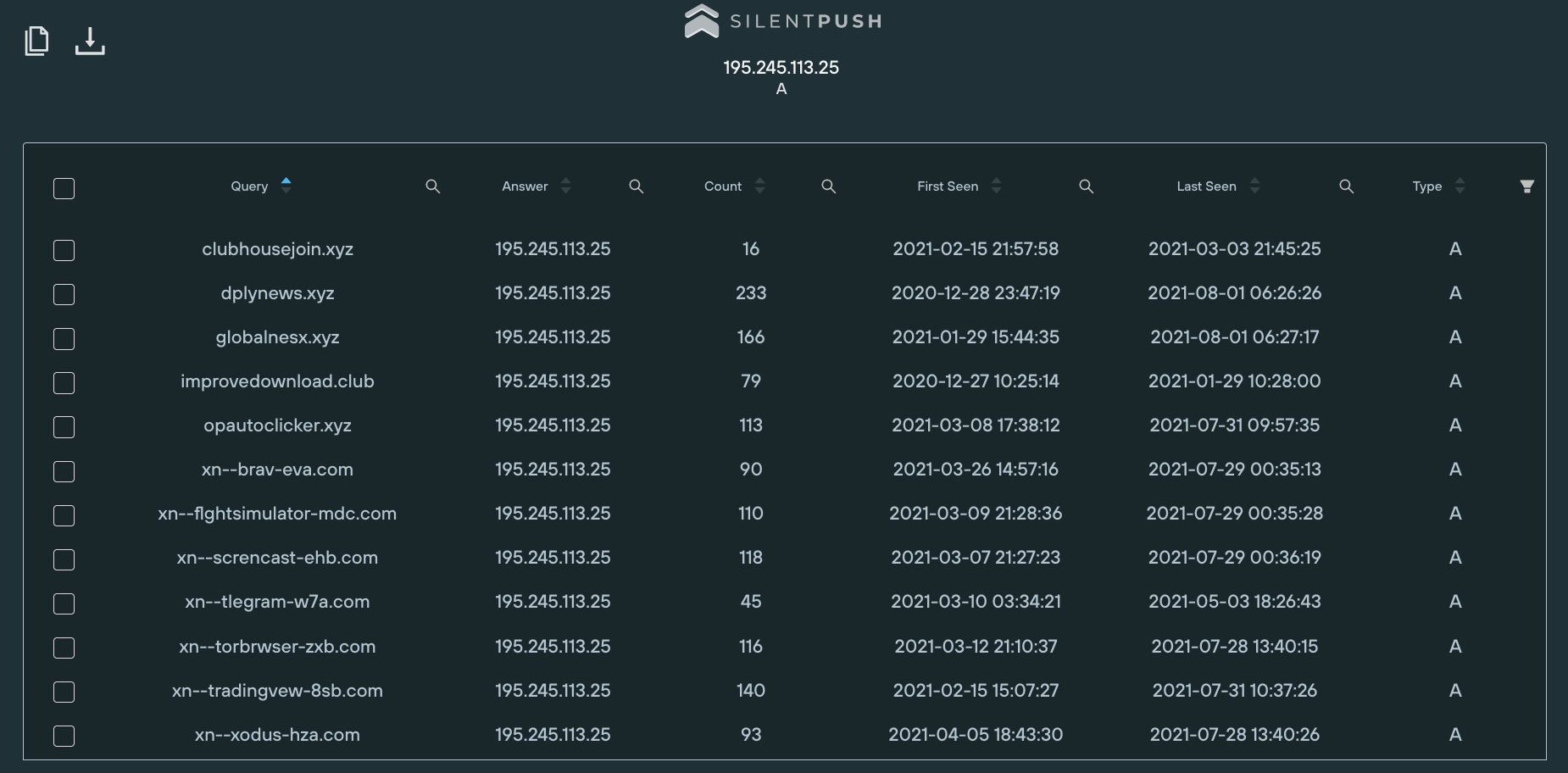
However, could this actor have hosted other domains at a different server? Assuming they’d also use the same registrar and hosting provider, a search query was ran in the Silent Push API for domains starting with xn-- using NameCheap’s name servers and hosted on ITLDC’s ASN (AS21100).
Nine further domains were found. Two of them (xn--80aaw7ah[.]com and xn--80ahcmbumt[.]org) represent words in the Cyrillic alphabet and there is no reason to assume they are used for anything malicious.
The other seven, however, were all hosted on the same IP address (195.245.113.25) and all impersonate legitimate products, including once again Brave and Telegram:
The fake installer on bravė.com that prompted this research was an ISO file that appears to contain a version of the Redline infostealer. That suggests it may be related to a campaign analysed by Morphisec last month, where Redline was also served packed inside an ISO through malicious Google ads, impersonating Telegram and other services. The domain names involved in that campaign were also registered through NameCheap.
As for IDNs, there are tools that help one find homograph attacks on an existing domain name. However, it is through a comprehensive and easily searchable passive DNS database that one can find a bigger picture of the campaign using a homograph attack.
Indicators:
xn--brav-eva.com
xn--brav-yva.com
xn--flghtsimulator-mdc.com
xn--ldgr-xvaj.com
xn--screncast-ehb.com
xn--sgnal-m3a.com
xn--teleram-ncb.com
xn--tlegram-w7a.com
xn--torbrwser-zxb.com
xn--tradingvew-8sb.com
xn--xodus-hza.com
185.198.166.104
195.245.113.25

